I’ve recently been investigating Azure Automation RunBooks. Essentially, this gives you a way to execute some code (currently Powershell or Python) to perform some basic tasks against your infrastructure.
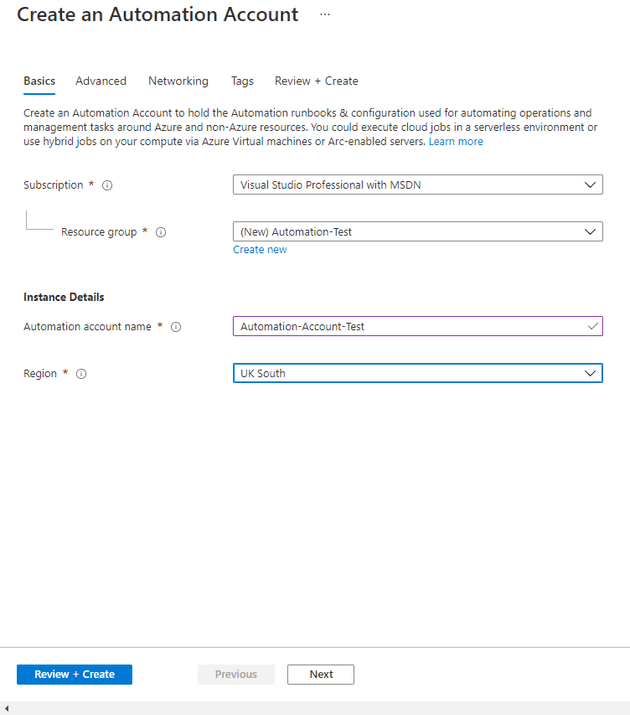
For this post, we’ll focus on setting up a (default) runbook, and just making it run. Let’s start by creating an automation account:
From here, you can create your automation account:
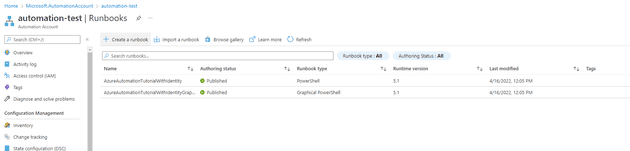
Once this creates, it gives you a couple of example run-books:
If we have a look at the tutorial with identity, it gives us the following Powershell Script:
<#
.DESCRIPTION
An example runbook which gets all the ARM resources using the Managed Identity
.NOTES
AUTHOR: Azure Automation Team
LASTEDIT: Oct 26, 2021
#>
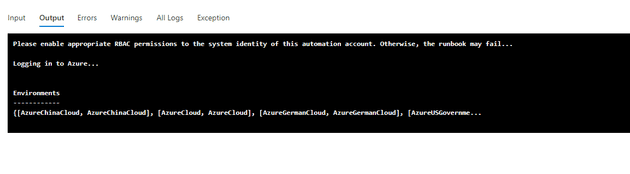
"Please enable appropriate RBAC permissions to the system identity of this automation account. Otherwise, the runbook may fail..."
try
{
"Logging in to Azure..."
Connect-AzAccount -Identity
}
catch {
Write-Error -Message $\_.Exception
throw $\_.Exception
}
#Get all ARM resources from all resource groups
$ResourceGroups = Get-AzResourceGroup
foreach ($ResourceGroup in $ResourceGroups)
{
Write-Output ("Showing resources in resource group " + $ResourceGroup.ResourceGroupName)
$Resources = Get-AzResource -ResourceGroupName $ResourceGroup.ResourceGroupName
foreach ($Resource in $Resources)
{
Write-Output ($Resource.Name + " of type " + $Resource.ResourceType)
}
Write-Output ("")
}
Looking at this script, it only really does two things: connects to Azure using managed identity, and then runs through all the resource groups in the subscription and prints them out.
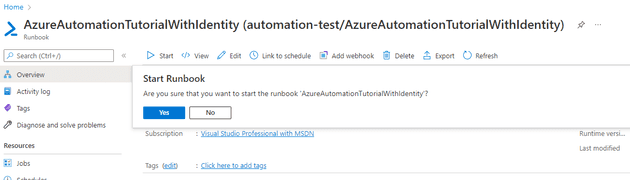
If you run this:
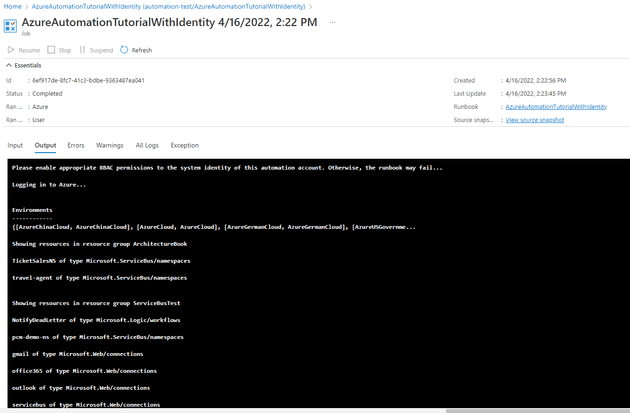
Then you’ll see the following warning in the output (basically saying that you should set-up the permissions, or things won’t work):
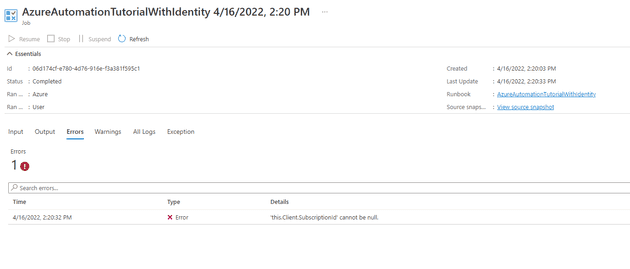
If you now switch to Errors, you’ll see a confusing error (caused by the fact that we haven’t set-up the permissions, and so things don’t work):
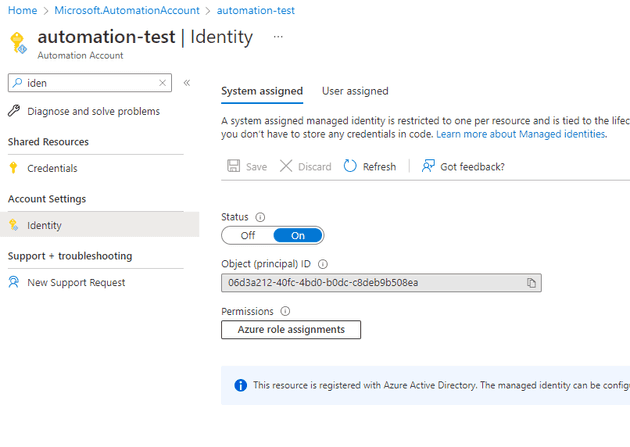
In order to correct this, you need to give the run-book appropriate permissions. Head over to the automation account resource, and select Identity:
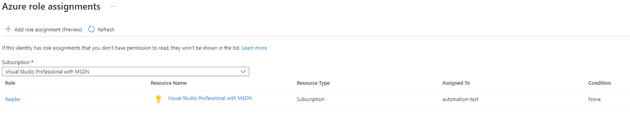
Select Add role assignments.
Because this script is listing the resources in the subscription, you’ll need to be generous with the permissions:
If you run that now, it should display all the resource groups fine: